Best and most demanding absolute alternatives will be discussed in this article. Absolute is the top supplier of endpoint resilience solutions that help businesses protect their people, data, and devices against online threats. The business’s specialised cloud-based technology helps defend against sophisticated threats, such as insider threats and zero-day assaults. It offers businesses a unified solution for managing and protecting their assets across all endpoints, from servers to mobile devices. Its technology circumvents the drawbacks of legacy or on-premise endpoint security solutions by being entirely automated and supplied over the cloud.
It is a straightforward, cost-effective, and effective cybersecurity solution for your expanding company. Using the same technology that 400 million users worldwide rely on, it defends your network from hackers. It offers a firewall to shield websites against denial-of-service and web exploit assaults. It guards against spear-phishing and spam email assaults and takes action against harmful email content. It offers the greatest cybersecurity solution overall.
Top 15 Best Absolute Alternatives in 2022
Top 15 Best Absolute Alternatives are explained here.
1. Business Antivirus Pro Avast
Avast Business Antivirus Pro is a business-oriented cybersecurity solution. It provides user-friendly, business-class defence against malware such as spyware and viruses. You may select a security level based on your company needs thanks to customisable options. In order to shield trustworthy apps from scanning, it establishes a whitelist. Additionally, it automatically quarantines infected files and data in a secure virtual environment until you decide to release it. It also schedules routine scans of a predetermined set of workstations. For SMBs, Managed Security Services Providers (MSSP), and enterprises, it offers comprehensive cybersecurity solutions. This is another absolute alternative.
It addresses new internet hazards to keep you one step ahead of hackers. Endpoint security is simply managed and deployed. It provides effective, cloud-managed security for desktop and laptop devices to safeguard each user. Additionally, it uses real-time threat detection and automated upgrades to safeguard each endpoint. It is powered by Avast, the biggest cybersecurity firm in the world with more than 400 million clients, and Threat Sense, a cutting-edge machine learning-based solution that can identify both known and unidentified threats. Also check live auction software
2. McAfee Endpoint Threat Defense and Response
Software called McAfee Endpoint Threat Defense and Response was created to find and eliminate threats on endpoints wherever they may be. A new pod architecture enables customers to deploy it across their entire organisation, from mobile devices to endpoints in the data centre, and it has a new user interface, deep integration with current data sources, advanced threat hunting using machine learning and artificial intelligence, and these are just a few of its features. It is a comprehensive endpoint environment security and management solution that guards against sophisticated attacks.
Real-time visibility is provided, and it enables quick reaction to threats before harm is done. It combines market-leading endpoint security with administration capabilities for quick and simple management of hundreds of endpoints. In order to assist assure real-time protection against malware, ransomware, spyware, viruses, rootkits, phishing assaults, and other threats, it makes use of artificial intelligence, machine learning, and threat understanding. It may be installed on any Mac or Windows endpoint without altering user workflow or posing additional security concerns.
3. Malwarebytes for Business
This is another absolute alternative. A business called Malwarebytes for Business creates anti-malware software to shield people and organisations against malicious software that harms computers running Microsoft Windows, including worms, trojan horses, rootkits, rogues, and frauds. Its products offer malware removal and prevention tools for enterprises as well as a free anti-virus scanning for home users. It is renowned for its free anti-malware software, which is offered to individuals, organisations, and small enterprises. It is a cyber security system that guards computers against harmful software such as viruses, spyware, and adware.
It is renowned for providing quick and efficient defence against PC hazards and threats, including computer viruses. For its ability to combat malware, it ranks as one of the best in its class. Using its security solutions, it has found and eliminated more than 6 billion malware threats from PCs. It is committed to defending customers and companies from harmful threats including malware, ransomware, and exploits that are undetectable by conventional antivirus programmes.
4. Protect Jamf
For macOS, Jamf Protect is an endpoint security solution. It combines strong and straightforward technologies that make use of machine intelligence to help safeguard your Mac and your clients. It offers security for both Mac users who control their own devices and companies that use Jamf-managed Macs. Jamf Protect safeguards your devices and data whether you’re a large corporation managing thousands of Macs or a school, hospital, or government agency giving Macs to your staff directly.
By automatically activating device compliance, it lowers maintenance costs while safeguarding macOS, iOS, and tvOS devices against malware and phishing threats. While protecting the data of your personnel, it can significantly lower the attack surfaces of your fleet. Check out the answer by downloading it and putting it to use. It enables you to locate infected macOS machines and, if necessary, ban them. It is created using a technical architecture that serves a goal.
5. Webroot Corporate Endpoint Protection
A platform called Webroot Corporate Endpoint Protection may be easily integrated into business applications. Using machine learning techniques, it can track the output of business applications in real-time and identify unusual patterns that can indicate malicious activity. Additionally, it offers cloud-based management solutions to centralise security processes and simplify them. Through enhanced threat intelligence, machine learning, advanced analytics, and behavioural analytics capabilities that can identify attacks across endpoints, it gives an enterprise-class solution to endpoint security. This is another absolute alternative. Also check forms automation software
Additionally, it offers connection with AWS Marketplace goods like Threat Intelligence Services and Amazon Inspector for extra security levels. It combines the strength of machine learning, artificial intelligence, and big data to identify patterns and behaviours employed in attacks. The service may be used in both small and big enterprises by combining cloud and on-premise deployment options. It offers defence mechanisms that stop viruses and malware.
6. Symantec Endpoint Security
The cybersecurity software package Symantec Endpoint Security was created by Symantec. The programme offers defence against several forms of malware, including worms, spyware, and viruses. Additionally, it offers security against rootkits and malware. It offers attributes like intrusion prevention and a firewall that are useful in thwarting attempts at illegal access to private networks. With its most complete endpoint security package, you may feel safe from online dangers while also safeguarding your identity, defending your devices from viruses, spyware, and other malware, and more.
In addition to PC backup and restoration, Symantec Endpoint Protection offers cloud and external drive data backup for users. Users are given the option to decide whether to delete backups after a specific length of time. Users have the option to specify the retention period for their backups using a feature. They have the option of keeping their backup for a single day, a week, a month, or even forever.
7. SentinelOne Singularity
Using cutting-edge artificial intellect and machine learning technology, SentinelOne Singularity is a next-generation security firm that can identify and thwart cyberattacks in real-time. Its sophisticated threat detection solution, Singularity, uses unsupervised machine learning to become wiser over time and may significantly help to enhance your security posture.
This is another absolute alternative. It is intended to identify and respond to the most important threats, including as zero-day, APT, and polymorphic threats, independent of their origin or level of complexity, without being slowed down by the numerous noise warnings typical of signature-based detection. It is a cybersecurity system based on artificial intelligence that employs machine learning and natural language processing to detect, follow, and forecast cyberattacks and unusual user activity. It enables staff at security operations centres to swiftly and effectively identify the most pertinent cyberattacks and take action to protect against them.
8. N-central
With the help of the cybersecurity solution N-central, you can establish a location where team members can communicate, manage risks, and adhere to rules. It provides a thorough, secure platform for cooperation for the personnel, operations, and data of your business. With the aid of its tools and services, businesses of all sizes can control employee access to privileged accounts, defend against online attacks, gather and analyse security data from all parts of the business, and adhere to stringent requirements like GDPR, NIST, FISMA, and PCI DSS.
Additionally, it provides a completely automated IT asset disposition service that aids businesses in getting rid of outdated IT assets that could be exposed to security risks. With the use of next-generation threat intelligence, its intelligent agent, Profiler, offers real-time defence against assaults on endpoints, browsers, and apps. It automatically recognises application vulnerabilities and sensitive data that may be exploited by attackers, as well as known and undiscovered malware, including fresh zero-day assaults.
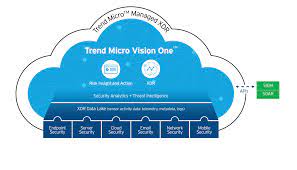
9. Trend Micro XDR
With the help of Trend Micro XDR, businesses can carefully regulate and encrypt their data while still securely exchanging it with the appropriate internal and external parties. It is a crucial part of Trend Micro’s safe digital transformation solution, which offers visibility and threat analysis, defends against intrusions, and aids in developing a cybersecurity culture throughout a business. It is an antivirus, application control, and device control security solution package that is constantly updated to protect people, data, and networks from the most cutting-edge threats. This is another absolute alternative.
It is an enterprise-class, multi-tenant, isolation-based security platform that is supplied via the cloud and offers defence for teams working in DevOps and SecOps. Organizations are now better able to train, deploy, and respond to emerging threats quickly thanks to a flexible deployment strategy created for agile cloud use. With the greatest customer support in the business, the architecture is also adaptable enough to offer security for any number of endpoints on any number of networks
10. Endpoint Protection
A cybersecurity product called Endpoint Protector aids remote employees and small businesses in protecting their equipment and data. It aids businesses in removing the risk of breaches and hacks, gives them visibility into network activities, and stops the usage of vulnerably out-of-date software on their network. It is a system that safeguards users’ privacy, security, and device performance while defending against cyberattacks, including zero-day threats.
It is able to accomplish this because it makes use of a special posture-based technology that categorises each activity that is currently operating and its associated communication patterns in order to construct a baseline of typical system operations. The product employs machine learning to detect deviations from the norm after establishing this baseline. It assists in protecting people and small organisations against dangers like as ransomware, malicious code, targeted assaults, and data loss on their computers, networks, and data. In order to make sure fixes are constantly up-to-date and free of malware, it also analyses for vulnerabilities and gives users the ability to safely control updates.
11. FireEye Endpoint Security
A cybersecurity system called FireEye Endpoint Security offers the best reaction to the shifting threat scenario. It is a cloud-based online and email security system with many engines that can identify and stop targeted threats and advanced threats. It safeguards Macs and PCs against hackers. In order to deliver end-to-end threat prevention across OS systems, browsers, applications, email, and the cloud, it connects with your current security software. By preventing or controlling cutting-edge threats like targeted assaults or zero-day exploits, it is intended to defend against cyberattacks before harm can be done. Also check Typhoo software
This is another absolute alternative. The zero-day malware of today and future, including never-before-seen malware and sophisticated persistent threats, are caught via vulnerability-based threat scanning. With the help of cutting-edge antivirus technology, it offers consumers endpoint real-time protection by thwarting both known and unidentified threats. It keeps track of how all programmes behave and which files they open or modify on a computer, and it stops any harmful activity or access to malicious data.
12. Cortex XDR
Security teams no longer have to manually scan and comprehend signals from various security systems thanks to Cortex XDR, a cybersecurity solution. In order to focus on the most sophisticated threats and progress toward a zero-trust environment, security teams must provide individuals the context they require to make judgments that are rapid and accurate. For both business and government, it serves as an application firewall, intrusion protection, and network intrusion prevention.
It is a security architecture that guards against data breaches and DDoS assaults, safeguards client information and proprietary information, and counters web-based attacks. A platform known as “Security-as-a-Service” aids in stopping the spread of malware and phishing tactics. Sensitive data is safeguarded from quantum computing by this network and application solution. It keeps track of all network connections, processes, and services to look for any irregularities that can assist stop zero-day assaults before any harm is done.
13. Ziften Endpoint Detection and Response
A cybersecurity system called Ziften Endpoint Detection and Response uses machine learning and behaviour analysis to stop malicious assaults on endpoints. In addition to provide visibility and control over programmes, users, and material, it focuses on cyberthreats that target user devices. Before data is lost or malware spreads, enterprises can identify, analyse, and eliminate endpoint risks with the aid of a special blend of proprietary behavioural detection technology and cutting-edge machine learning. This is another absolute alternative.
Companies can segregate troubled users from the network with this software while still offering assistance to those who require it. It has earned the trust of corporations all over the world and is intended for businesses with enterprise endpoint security requirements. It was created with the network administrator in mind, who regularly has to deal with overly zealous security managers and disobedient users who don’t want to follow security standards.
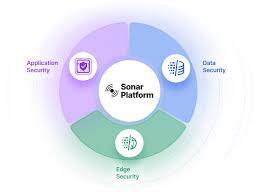
14. Imperva Sonar
Imperva Sonar is a high-end software programme that automates procedures and gives you tools for safeguarding an organization’s systems, applications, and data. Your downtime is reduced and your data is protected from DDoS attacks. This platform may be used to safeguard your application by establishing a firewall and enhancing operational procedures. It assists you in safeguarding your applications in a number of ways, including runtime security, API security, high-level bot security, serverless security, etc.
It offers cloud solutions and safeguards your data in a cloud setting. Database risk & compliance, data user activity analytics, data privacy, and many more elements are included in its data protection capabilities. Imperva Sonar would be your finest choice if you’re seeking for a comprehensive solution to defend your business against any sort of assault.
15. Quantum Network Security
With capabilities that can manage the operation of any size business, Quantum Network Security is a cloud-based security software solution that addresses all areas of the company’s security. It defends against high-level attacks and gives you access to hyper-scale threat protection for your company. This programme has network management access and unified security features that can help you improve IoT productivity. This is another absolute alternative.
Your IT staff can easily connect it with your systems because its deployment and maintenance are so straightforward. Additionally, by enabling VPN access, you can safeguard your remote users. With its extensive dashboard, you may manage every aspect of operation from a single screen. Therefore, due to its high-level and user-friendly features, Quantum Network Security is the finest